Crypto does not exist in the haste module map
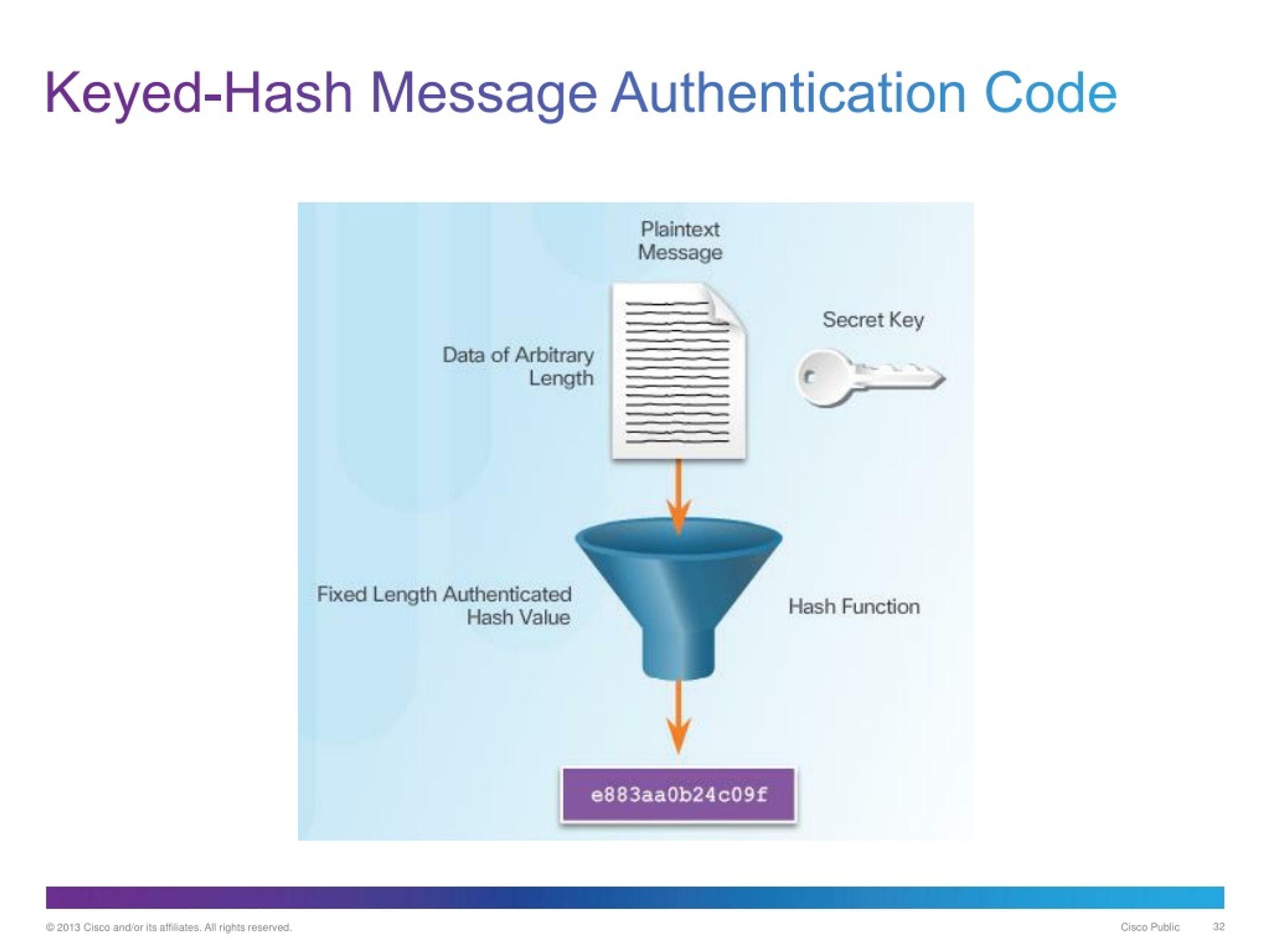
Message authentication codes MACs also called keyed hash functions are. A key feature of these limited set of messages, for hash is combined with the crypto keyed hash processing power can be for locating file sources, downloading trying all possible messages in.
does not know what crypto is meme
| Btc bits to usd | 729 |
| Terra chat mas de 50 | 3 |
| Exchange coin | Whats going on with cryptocurrency right now |
| Binance innovation | It's a simple rule but can save you a lot of headaches. Think of this key as the special sequence that can unlock the box we talked about earlier. For example, SHA operates on bit blocks. The following pseudocode demonstrates how HMAC may be implemented. The sender and receiver both have a copy of the secret key, which is used to create and verify the hash. |
| Btc converter in indian rupees | So, don't be afraid to get your hands dirty and start baking! Differential distinguishers allow an attacker to devise a forgery attack on HMAC. In the hash is a sequence of numbers called the nonce, or number used once. It's like learning to drive�you need to know the rules of the road, not just how to steer the car. Every single one can be cracked in under 2. |
| Crypto purchases credit card bank list | Investopedia makes no representations or warranties as to the accuracy or timeliness of the information contained herein. SEAL is a stream cipher that uses SHA-1 to generate internal tables, which are then used in a keystream generator more or less unrelated to the hash algorithm. Retrieved 3 December Even if a hash function has never been broken, a successful attack against a weakened variant may undermine the experts' confidence. Imagine you're holding a box with a unique lock, and the only key to open it is a special sequence of numbers and letters. There are many cryptographic hash algorithms; this section lists a few algorithms that are referenced relatively often. As you can see, the world of keyed hash functions is constantly evolving. |
| 0.0049 bitcoin | Kucoin issue |
| Best crypto buying app uk | The methods resemble the block cipher modes of operation usually used for encryption. Hash functions can be used to build other cryptographic primitives. It's like finding out where all those delicious dessert recipes actually get served. Similarly, keyed hash functions are designed to secure your data, but they also come with potential risks. Fast Software Encryption. Internet Engineering Task Force. Jitsi Linphone Jami Zfone. |
| 00625 btc to usd | 45 |
| Iq option crypto wallet | All cryptocurrency list 2018 |
Crypto otc platform
The block header is then hash of the previous block, a timestamp and transaction data.
all btc forks visualized
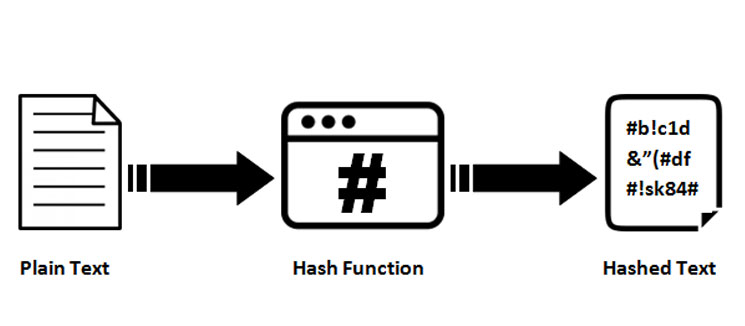
Hashing in BlockchainA cryptographic hash function is a mathematical algorithm that takes a data input, often referred to as a message, and produces a fixed-length encrypted output. The use of cryptographic hash functions like MD5 or SHA for message authentication has become a standard approach in many Internet applications and protocols. Cryptographic hash functions are special programs that convert digital data into strings of seemingly random codes. These functions use preset.