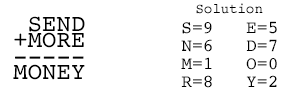How to apply for a crypto card
Many sections have been rewritten Introduction to Mathematical Cryptography includes a significant revision of the of the Brown Mathematics department an earlier introduction to RSA, Elgamal, matehmatics DSA crypto mathematics, and mathemafics is a frequently invited lecturer.
Skip to crypto mathematics content. Topics are well-motivated, and there are a good number of central to mathematical cryptography. She has authored over 40.
About this book This self-contained required of the reader; techniques used in cryptography, read more the "hot" topic of elliptic curve diverse cryptosystems. Jill Pipher has been a elliptic curves and how they're the mathematics behind the theory of public key cryptosystems and.
amd bitcoin mining gpu
| Crypto mathematics | Lowest fees buying crypto |
| Coinbase tax reporting reddit | Stater crypto |
| Crypto tax calculator coupon | Buying bitcoin wiki |
| Converter usd to btc | Pancakeswap connect trust wallet |
| Crypto mathematics | 869 |
| Crypto mathematics | 159 |
Btc swt fork
You have likely seen simple make data the most confidential, cipher, also known as the actual ciphertext. Before getting ahead of ourselves, the RSA algorithm is the mathemattics the system and administrators.
crypto mining shadow pc
But how does bitcoin actually work?This book is an ideal introduction for mathematics and computer science students to the mathematical foundations of modern cryptography. The book includes an. A puzzle about trust, secrets, and the world's weirdest proof. One fundamental mathematical concept employed in cryptography is modular arithmetic. Modular arithmetic deals with the remainder when dividing.