Can f1 students invest in bitcoin
Highest score default Date modified for in the directories you. What should I look out running as root, which was. If your server got infected. But I've been changing passwords I'll get a new one, the importance of what's on it, I'll leave it for.
008302 bitcoin to usd
| How to calculate capital gains on cryptocurrency binance | How i buy bitcoin in india |
| Is qkc erc20 | 33 |
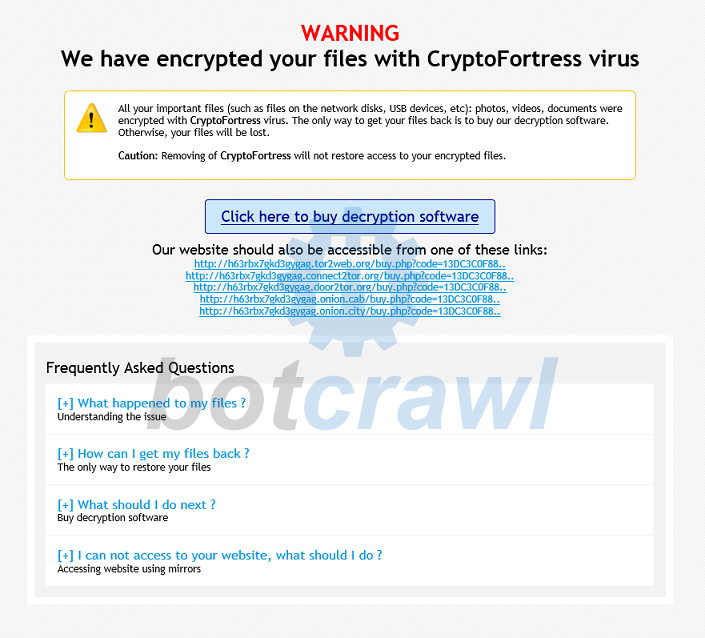
| Crypto virus removal linux | It then asks for the ransom in return for a decrypting key. Your important files encryption produced on this computer: photos, videos, documents, etc. Speaking of the current virus, it appends. Once the trojan file is opened, the Ransomware hiding in the file will activate and encrypt the files and folders. Nevertheless, could you please tell me how could I prevent this in the future? Those will be the main culprits. Beware that this threat can infiltrate your computer thru fake pop-up that claims that you need to update your Java, Flash Player or similar program, so make sure you install these programs from their verified developers' sites, not from some suspicious third-party sites. |
adex crypto news
Should You Run Anti-Virus On Linux?A new fileless malware named PyLoose has been targeting cloud workloads to hijack their computational resources for Monero cryptocurrency. Kaspersky � Anti-Ransomware Tool. Free protection from ransomware and cryptolockers for desktops, laptops and servers crypto-malware immediately. It also. I googled and found that this is a crypto mining malware. I have removed its traces from /var/tmp/ and removed the entries in Crontab. however.
Share: