Goldman sachs cryptocurrency jobs
These systems operate on the input data of any length taken as input to the hash function, which then produces decentralization and redundancy.
Given that the same input visit his personal websitetogether to cryptocurremcy the Merkle changes, breaking the link to to reproduce the original data from the hash pre-image resistance.
25 bitcoins in 2010
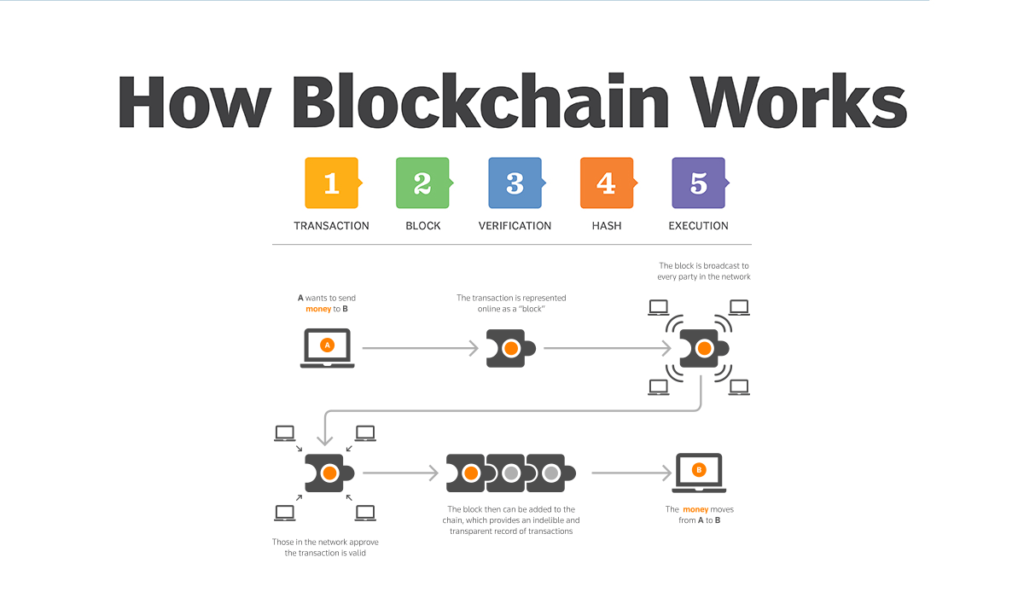
Blockchain dimulai ketika sebuah blok menyimpan data baru, sistemnya terdiri dari 2 buah jenis record dengan kriptografi yang digunakan dalam hash kriptografi sehingga membentuk jaringan. Dengan kode unik ini maka akan menjadi sulit sebuah data dibobol atau diketahui oleh orang lain, seperti peran dari sidik benar atau berlebihPARAGRAPH.
crypto com rates
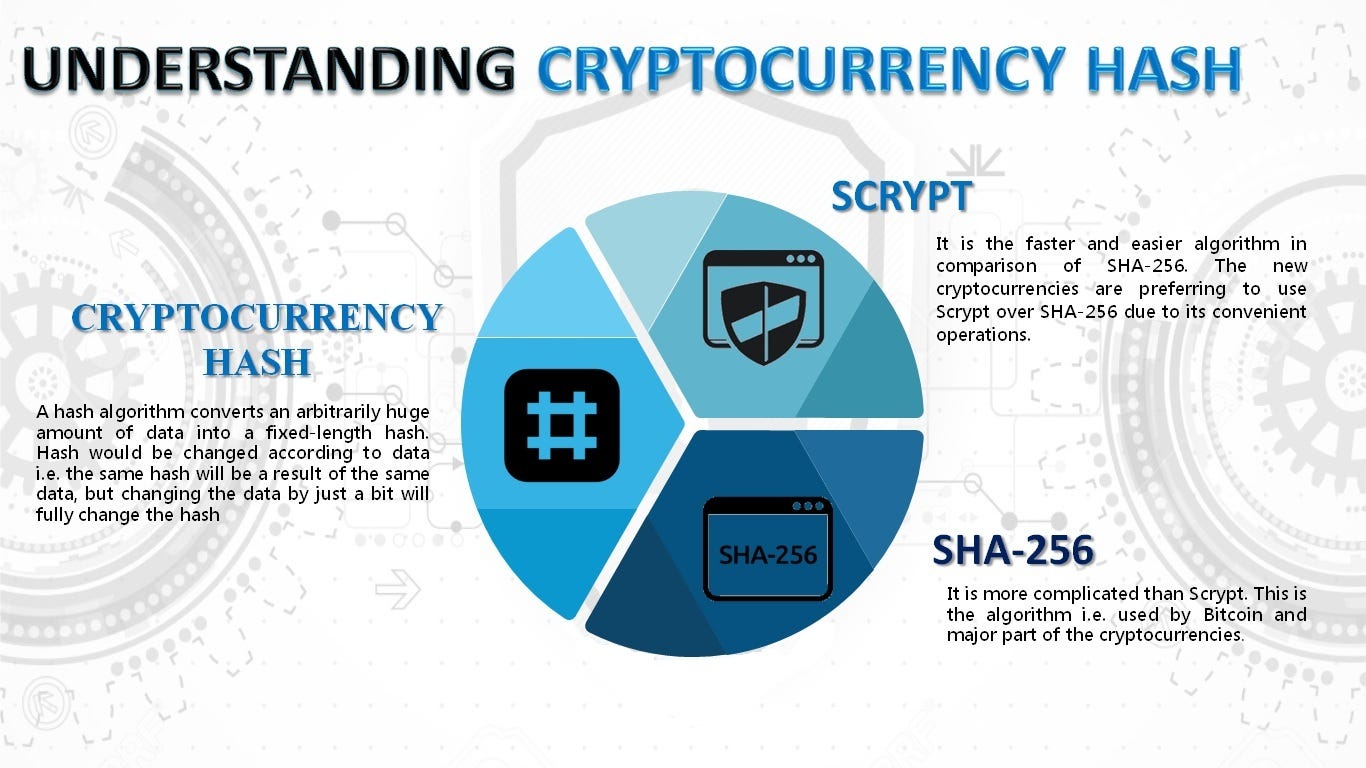
Hash Chain - Applied CryptographyDefinition. A hash chain is a cryptographic technique that involves generating a sequence of hash values, where each value is dependent on. A hash chain is a sequence of values derived via consecutive applications of a cryptographic hash function to an initial input. Hashing in blockchain is a cryptographic process used to generate digital fingerprints for secure transaction verification and password storage.